Introduce
Hello, to continue this series on basic security, this time I will introduce you to Email Spoofing, it means sending email with a fake address. I will show you how email spoofing can be dangerous for users.
Email is sent through Simple Mail Tranfer Protocol (SMTP) , SMTP does not have an authentication mechanism, so hackers often send emails by using fake addresses to trick the recipient of the email sender.
A common attack method is phishing – an attempt to trick users into sharing their login information. Phishing emails will often warn users that someone tried to access their account and ask them to change their password immediately.
However, the password change link redirects the user to the malicious website with a gmail-like interface.
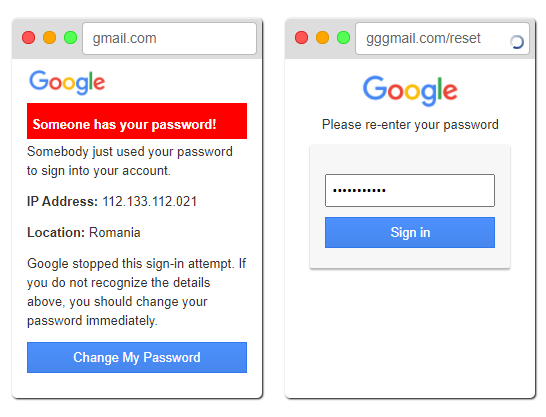
The user will then need to enter the old password, and it will be saved in the hacker database. The site will then redirect to the real password reset page, so the user is not in doubt.
Protection against phishing emails is largely due to your email service provider. Email service providers devote a lot of resources to trying to detect spam and malicious email.
Risks due to
In general, this is a very common and dangerous form of fraud. More than 95% of emails sent over the internet are email spam. Most spam uses fake addresses. If your domain is being used in spam messages, spammers may be using your users to:
- Stealing their login information by sending “phishing” messages.
- Taking advantage of users’ trust in our website to commit fraud.
- Distributing malware by sharing malicious files.
- And so forth and clouds …
Protect
As the website owner, you should prevent your domain’s use in spam by using both of the following methods:
1. Deploy Sender Policy Framework (SPF) :
Publish DNS records to specify which servers are allowed to send emails from your domain.
By changing your DNS records to the Sender Policy Framework (SPF) , you can specify which servers are allowed to send emails from your domain. This will help flag fake emails sent by scammers. For example:
1 2 3 | // mail chỉ có thể gửi từ những địa chỉ được liệt kê example.net. TXT "v=spf1 mx a:pluto.example.net include:aspmx.googlemail.com -all" |
2. Deploy Domain Key Identified Mail (DKIM) :
By using Domain Key Identified Mail (DKIM) , you can prove that the email is properly sent from your domain and that the email hasn’t been modified in transit.
DKIM adds a digital signature to the email header. The recipient of the message will check the signature upon receipt to verify that the message is authentic and has not been tampered with.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 | <span class="token comment"># @return [DkimHeader] Constructed signature for the mail message</span> <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">dkim_header</span></span> dkim_header <span class="token operator">=</span> <span class="token constant">DkimHeader</span> <span class="token punctuation">.</span> <span class="token keyword">new</span> <span class="token keyword">raise</span> <span class="token string">"A private key is required"</span> <span class="token keyword">unless</span> private_key <span class="token keyword">raise</span> <span class="token string">"A domain is required"</span> <span class="token keyword">unless</span> domain <span class="token keyword">raise</span> <span class="token string">"A selector is required"</span> <span class="token keyword">unless</span> selector <span class="token comment"># Add basic DKIM info</span> dkim_header <span class="token punctuation">[</span> <span class="token string">'v'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token string">'1'</span> dkim_header <span class="token punctuation">[</span> <span class="token string">'a'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> signing_algorithm dkim_header <span class="token punctuation">[</span> <span class="token string">'c'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> header_canonicalization <span class="token delimiter tag">}</span></span> / <span class="token interpolation"><span class="token delimiter tag">#{</span> body_canonicalization <span class="token delimiter tag">}</span></span> "</span> dkim_header <span class="token punctuation">[</span> <span class="token string">'d'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> domain dkim_header <span class="token punctuation">[</span> <span class="token string">'i'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> identity <span class="token keyword">if</span> identity dkim_header <span class="token punctuation">[</span> <span class="token string">'q'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token string">'dns/txt'</span> dkim_header <span class="token punctuation">[</span> <span class="token string">'s'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> selector dkim_header <span class="token punctuation">[</span> <span class="token string">'t'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token punctuation">(</span> time <span class="token operator">||</span> <span class="token builtin">Time</span> <span class="token punctuation">.</span> now <span class="token punctuation">)</span> <span class="token punctuation">.</span> to_i <span class="token comment"># Add body hash and blank signature</span> dkim_header <span class="token punctuation">[</span> <span class="token string">'bh'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> digest_alg <span class="token punctuation">.</span> digest <span class="token punctuation">(</span> canonical_body <span class="token punctuation">)</span> dkim_header <span class="token punctuation">[</span> <span class="token string">'h'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> signed_headers <span class="token punctuation">.</span> join <span class="token punctuation">(</span> <span class="token string">':'</span> <span class="token punctuation">)</span> dkim_header <span class="token punctuation">[</span> <span class="token string">'b'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token string">''</span> <span class="token comment"># Calculate signature based on intermediate signature header</span> headers <span class="token operator">=</span> canonical_header headers <span class="token operator"><</span> <span class="token operator"><</span> dkim_header <span class="token punctuation">.</span> to_s <span class="token punctuation">(</span> header_canonicalization <span class="token punctuation">)</span> dkim_header <span class="token punctuation">[</span> <span class="token string">'b'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> private_key <span class="token punctuation">.</span> sign <span class="token punctuation">(</span> digest_alg <span class="token punctuation">,</span> headers <span class="token punctuation">)</span> dkim_header <span class="token keyword">end</span> |
There is also a standard called Domain-based Message Authentication, Reporting & Conformance (DMARC ) that you should know. Read more here
Applying these technologies makes the email you send less likely to be marked as spam.
Configuration
Implementing SPF and DKIM requires publush new DNS records and make configurations to your technology stack – refer to the email service or software documentation for details. Below are related documents for some of the more common email delivery methods.
Transactional Email Services
Transaction Email is sent programmatically in response to web or app actions. If your website uses transaction email (for example, during registration or password reset), you need to make sure that you are sending authenticated emails. Here’s how to set up authenticated email in the top transactional email services.
Email Marketing Services
Email Marketing Services allows to send mass emails to mailing list. If you use this type of service, you need to ensure that the email sent is authenticated.
Mail Transfer Agents
System administrators use the software “Mail Transfer Agent.” The most common MTAs are Microsoft Exchange (on Windows) and SendMail / Postfix (on Linux).
summary
Above is the basic introduction to Email Spoofing, hopefully it will be useful for you. Happy coding !!!
