Dangerous application to access bank accounts, those who often watch YouTube need to pay special attention!
- Tram Ho
First discovered in June last year, malicious code called Nexus is now being publicly advertised by attackers on hacker forums to increase the reach of victims. The main targets of the ringleaders are 450 banking apps and crypto wallets.
The malware is being distributed through fake installs of YouTube Vanced, a third-party YouTube app that was once popular but now discontinued. Once installed on the victim’s computer, the malicious code will steal their banking information and thereby take the money in the account (Image: Cyble Research and Intelligence Labs – CRIL)
“Nexus appears to be in the early stages of development,” Italian cybersecurity firm Cleafy said in a report published this week.
“Nexus provides all the key features to perform ATO (Account Takeover) attacks against banking gateways and crypto services, such as stealing credentials and intercepting SMS. “
This Trojan appeared on various hacker forums earlier this year and is for sale for a monthly subscription fee of $3,000. Details of the malware were first documented by Cyble earlier this month.
However, there are indications that this malware may have been used in attacks since June 2022, at least six months before it was officially listed for sale on the black market. The malware is also believed to be a duplicate of another banking trojan called SOVA.
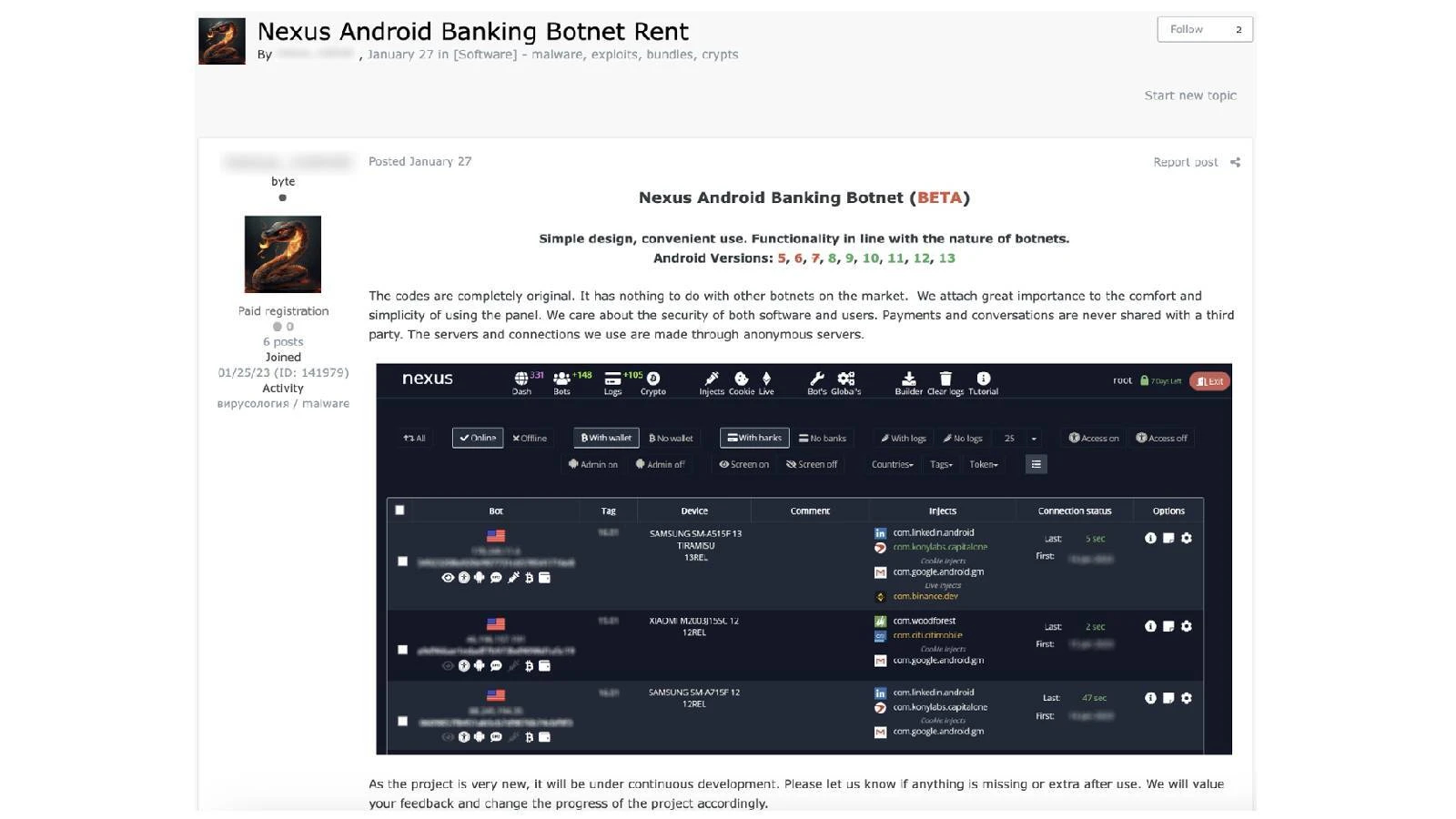
This malicious code is currently being sold on hacker forums and black markets (Image: Cyble Research and Intelligence Labs – CRIL)
Like other banking trojans, the Nexus app also contains features to hijack banking and crypto-related accounts by performing desktop notification fake attacks. and track keyboard travel to steal user credentials.
Furthermore, it is capable of reading two-factor authentication (2FA) codes from SMS messages and the Google Authenticator app through abusing Android accessibility services.
Some other notable functions are the ability to delete received SMS messages, activate or stop the 2FA code stealing module, and update itself by periodically pinging the command and control server (C2).
Source : Genk
