Introduce
CSRF is an attack method by which hackers take the authentication rights of a user to send requests that the user did not want. Through social networks or email, hackers can send links to users and trick users into taking actions as directed by hackers. A successful CSRF attack can trick users into transferring money, changing email addresses, etc.
Describe how to attack
To successfully perform a csrf attack requires 3 main factors:
- User Actions: The first condition of csrf is that the user must perform the desired action of the hacker (click on the dangerous link ….)
- Session handling based on cookies: the server determines the user’s http request using only cookies. There is no other mechanism for session tracking or validating a user’s request.
- The http request params do not include an unpredictable parameter. To understand more about this attack you can see the illustration below.
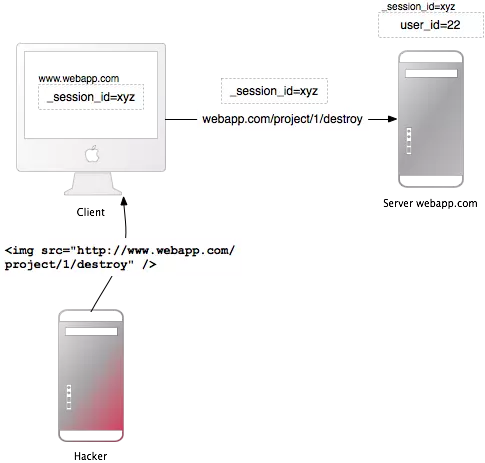
Here hacker sends an img tag with source leading to ” http://www.webapp.com/project/1/destroy ” to the user of the website ” http://www.webapp.com ” that the new user authenticates. before (session has not expired).
When the user clicks on the img tag sent by the hacker, the browser will send a request to delete project with id 1 to ” http://www.webapp.com ” together with the cookie of the user authenticated by the user on this website first Therefore, the server will delete the project with id equal to 1 without the user knowing.
CSRF attacks a targeting function that causes changes in user data on the server, such as changing a user’s email address or password or buying something.
How to prevent CSRF attacks
Server side
Use CRSF TOKEN
- By adding csrf-token to the form every time a user submits to the server it sends the csrf-token so it is possible to identify the request sent from that page. csrf-token must be unpredictable, each request will have its own token.
Use http method properly
- do not use the get method for data creation and update operations
Use a separate cookie for the admin page
- It is recommended to leave the admin page in a separate subdomain so that they do not share cookies with the front end of the product. The example should be set as admin.website.vn or better than website.vn/admin
User side
- Should get rid of important websites: Bank accounts, online payments, social networks, gmail, facebook… when you have finished the transaction or the work to be done. (Check email …)
- Do not click on untrusted links that you receive via email, facebook …
- Do not save information about passwords in your browser (do not choose the methods “next login”, “save password” …
- During transactions or important websites, should not visit other websites, which may contain exploit codes of attackers.
