Introduce
OpenID Connect is a simple identification layer built on OAuth 2.0 protocol. OAuth 2.0 defines mechanisms to obtain and use access tokens to access protected resources, but they do not define standard methods for providing identity information. OpenID Connect performs authentication as an extension to the OAuth 2.0 authorization process. It provides information about end users in the form of id_token to verify a user’s identity and provides basic profile information about the user.
OpenID Connect is our recommendation if you are building a web application that is hosted and accessed via a browser.
Register the AD tenant application
First, register your application with the Azure Active Directory tenant (Azure AD). This will provide the application ID for your application, as well as allow it to receive the token.
- Log into the Azure portal .
- Select the AD tenant how to select your account in the top right corner of the page, then select the Conversion Directory navigation and then select the appropriate tenant.
- Skip this step if you only have one Azure AD tenant in your account or if you selected the appropriate Azure AD tenant. In the Azure portal, search and select Azure Active Directory.
- In the left menu of Azure Active Directory, select Application Registration, then select New Registration.
- Follow the instructions and create a new application. It doesn’t matter if it’s a web client or a public client (mobile & desktop) for this tutorial, but if you want specific examples for web applications or public clients , check out our quick start.
- The name is the application name and describes your application to end users. Under Supported account types, select Accounts in any organizational folders and individual Microsoft accounts. Provide the redirect URI. For web applications, this is the base URL of your application where users can log in. For example http: // localhost: 12345 . For public clients (mobile and desktop), Azure AD uses it to return token responses. Enter a specific value for your application. For example http: // MyFirstAADApp . Once you have completed the registration, Azure AD will assign your application a unique customer identifier (application ID). You need this value in subsequent sections, so copy it from the application page.
- To find your application in the Azure portal, select Register applications, then select View all applications.
Stream authentication using OpenID Connect
The most basic login flow contains the following steps – each of which is described in detail below. 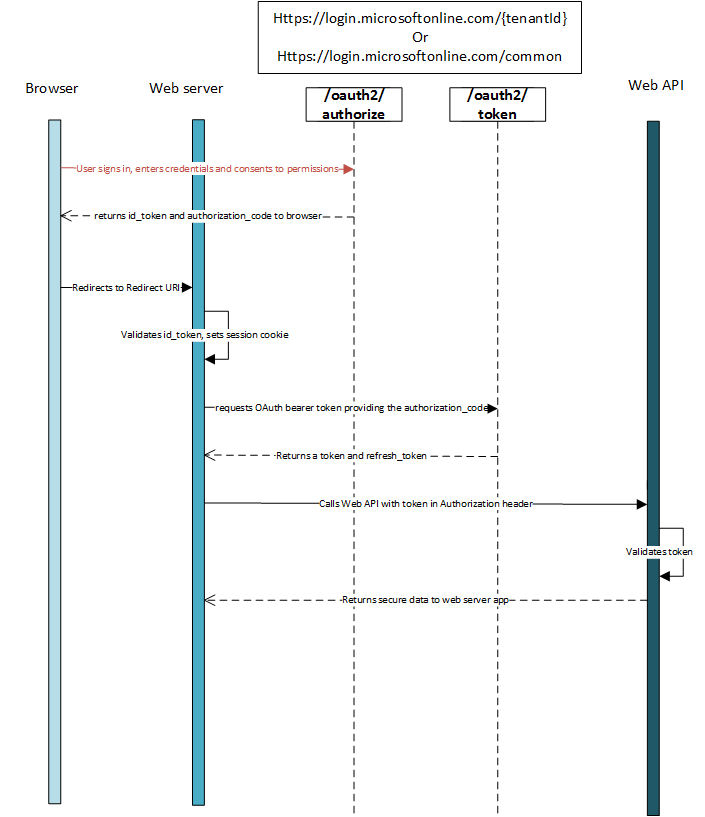
OpenID Connect metadata document
OpenID Connect describes a metadata document that contains most of the information needed for an application to perform login. This includes information such as the URLs to use and the location of the public signing keys of the service. OpenID Connect metadata documentation can be found at: https://login.microsoftonline.com/{tenant}/.well-known/openid-configuration
Metadata is a simple JavaScript Object Notation (JSON) document. See the following excerpt for an example. The content of the excerpt is fully described in the OpenID Connect specification. Note that providing the tenant ID instead of the common {tenant} above will result in tenant-specific URIs in the JSON object being returned. { "authorization_endpoint": "https://login.microsoftonline.com/{tenant}/oauth2/authorize", "token_endpoint": "https://login.microsoftonline.com/{tenant}/oauth2/token", "token_endpoint_auth_methods_supported": [ "client_secret_post", "private_key_jwt", "client_secret_basic" ], "jwks_uri": "https://login.microsoftonline.com/common/discovery/keys" "userinfo_endpoint":"https://login.microsoftonline.com/{tenant}/openid/userinfo", ... }
If your application has a custom signing key due to the use of the complaint mapping feature, you must append the query parameter containing the application ID to get jwks_uri pointing to the application’s signature key information. For example: https://login.microsoftonline.com/{tenant}/.well-known/openid-configuration?appid=6731de76-14a6-49ae-97bc-6eba6914391e jwks_uri https://login.microsoftonline.com/{tenant}/discovery/keys?appid=6731de76-14a6-49ae-97bc-6eba6914391e
Reference: Authorize access to web applications using OpenID Connect and Azure Active Directory
