
1. Concepts
Bring Your Own Device (BYOD) – Allows employees to bring personal devices such as laptops, cell phones, tablets … to work.
With BYOD, instead of working with multiple devices at the same time, or constantly switching between devices, you just need to use the individual device.
This is a mutually beneficial approach. Allowing employees to equip themselves with equipment helps businesses save a significant amount. On the other hand, this also helps to improve employee productivity.
This is a new trend, appearing in many countries, not just Vietnam.
2. Why BYOD has become a trend?
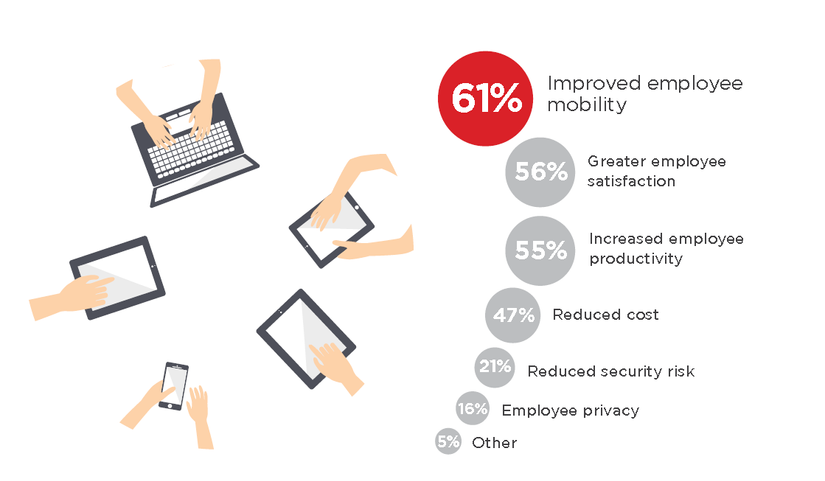
Improving working efficiency for employees and saving costs is the top priority of the business. Therefore, BYOD has become a trend chosen by many businesses.
Others are still hesitant about allowing employees to use personal devices for work, because they think this will distract work, causing unpredictable security risks. Indeed, Forbes’ survey data shows the opposite:
- 49% of surveyed employees say they work more efficiently on their personal devices.
- 78% of employees surveyed believe that using a single and consistent device helps them balance better between work and personal life.
- 82% of employees believe that mobile phones play an important role in boosting work productivity.
Thanks to BYOD, flexibility in work is enhanced. Employees can connect and handle basic tasks such as answering emails, supporting customers, interacting with colleagues … anytime, anywhere, even when not in the office. From there, improve the quality and speed of the employees’ work. According to statistics from Cisco Service Dynamic, employees who use a device for both personal and work purposes, are 2 times more productive than those who use separate equipment.
Allowing the use of personal devices in the office environment also demonstrates the degree of trust that businesses have in their employees. Therefore, an effective BYOD policy not only helps to minimize the cost of equipment and facilities investment, but also enhances the employee’s satisfaction level with the enterprise.
With their own devices, employees can easily master the usage. These devices are often equipped with the latest technologies, hardware is regularly upgraded, so it requires employees to be sensitive to new technologies. This will be very beneficial for jobs especially jobs that are constantly changing in technology.
3. Security risk caused by BYOD

BYOD is a challenge for businesses in data management because they contain numerous threats to data security. What most businesses worry about is the risk of employees losing or dropping devices and someone can use them to access business resources.
Data can be stolen when employees leave the company. According to Symantec’s 2013 study, more than 50% of employees surveyed tend to steal company data when they quit their jobs. And 40% of them intend to use them for new jobs. The explosion of BYOD has made it increasingly simple for employees to leave with sensitive organizational data.
Personal devices also pose great security risks when connected to a corporate network:
- It is very difficult to identify the users accessing the network.
- The device runs on many different platforms, making it difficult to have complete security measures.
- Personal devices are a favorite target for attackers. They have a higher risk of virus infection from applications, malware. Extend the range of attacks via email or social networks.
- When accessing the network, the access information remains on the device even when the user stops connecting.
4. BYOD security
BYOD increases productivity and saves a lot of costs for businesses, but it poses a number of security issues. Since BYOD devices are not strictly controlled by the organization, the information stored therein may be unsafe, increasing the risk of data breaches. If something goes wrong, it’s also more difficult to fix, especially when employees are allowed to use many different devices.
With BYOD, it is not possible to have a unified support system for all devices, because employees work on multiple devices with a high diversity. Businesses need to understand and be aware of this to come up with solutions when problems arise most effectively.
Security is the current top priority for all areas and BYOD is not out of that scope, but this challenge is huge, hard to overcome. The data security department must always be on hand. Antivirus programs and passwords need to be set.
Every business needs to know that no security tools or methods are absolute, but rely mainly on people. Every employee should be aware that they are holding important information, and that they are responsible for the data stored on their devices. At the same time, businesses need to clearly inform employees that it is a crime to obtain confidential corporate data.
The lack of cooperation between employees and businesses is the biggest factor leading to data leakage to the outside. Even an employee who is satisfied with his job can cause data loss due to lack of understanding or carelessness. However, disgruntled employees are more likely to steal data when they leave the company. According to research by the Ponemon Institute, more than 60% of survey results show that data theft is mostly caused by negative views of employees’ old companies.
Using mobile phones, personal tablets for work is an irreversible trend, so instead of fighting, businesses need to look at their positives and overcome the weaknesses they cause. BYOD is not simply enabling employees to use their personal devices at work, but it is the acceptance of users to access business resources from their personal devices safely and securely. The long-term approach is to organize courses for staff so that learners can identify vulnerabilities that are at risk of exploitation, and countermeasures and remedies.
When accepting BYOD, businesses must consider building appropriate security measures, both ensuring security for the business, and respecting the personal issues of employees:
- Specifying allowed devices: Devices are very diverse so it is important to be clear which ones are allowed to use.
- Set up strict security policy for all devices: When phones or other devices are connected to the server, a lot of sensitive information can be accessed. If employees want to apply BYOD, they need to be willing to set strong passwords to protect the equipment.
- Define clear policies for devices: What support will be provided for broken devices? What is the support policy for personal devices? …
- Clear information about data storage: If problems arise, the most effective method is to delete all the data on the device. However, that includes personal data. Therefore, when something goes wrong, it is necessary to notify employees of erasing data on the device and instruct them how to secure their device and back up the information for recovery.
- Specify which apps are allowed and forbidden to install: This rule should apply to any device that can connect to the Server, not only personal devices but also corporate devices. Also pay attention to copyrighting apps with personal devices.
- Data control when employees quit: When an employee leaves the organization with a device that is allowed to connect to the network, access to organizational data. The organization needs to eliminate all data, access rights with accounts and applications. This is not easy because the staff does not need to leave personal equipment. Some businesses deal with this by disabling all business accounts that provide data access. Employees with a high sense of security will voluntarily perform the above actions when leaving the company.
BYOD has both advantages and disadvantages, but its ever-increasing popularity requires businesses to proactively face them. This is a challenge but also a new opportunity for businesses.
