As the strongest security layer for iPhones and iPads, it turns out Apple’s Secure Enclave chip has an unpatchable flaw.
- Tram Ho
One of the main layers of protection Apple has provided to its devices over the years is the Secure Enclave security chip, which encrypts and protects all important data stored on the device. Last month, however, some hackers claimed that they had found an “unpatchable” flaw in the chip, threatening data security on a range of devices, from iPhones, iPads to MacBooks.
What is the Secure Enclave chip?
Secure Enclave is a security co-processor that is included in most Apple devices as an additional layer of security. All data stored in iPhone, iPad, Mac, Apple Watch and other Apple devices will be encrypted with random private keys, accessible only by Secure Enclave chips. These keys are individually designed for each device and they are never synchronized with iCloud.

The data stored in Secure Enclave will be completely separate from the system
Not only does it encrypt your files, Secure Enclave is also responsible for storing security keys to manage sensitive data, such as passwords, credit cards used for Apple Pay and even biometric credentials. Biometric for Face ID and Touch ID. This makes it difficult for hackers to access your data without a password.
It is worth noting that although the Secure Enclave chip is built right into the device, it works completely separate from the rest of the system. This is to ensure that the application will not have access to your private keys, forcing them to go through the Secure Enclave chip to send requests for decoding special data such as fingerprints, instead of accessing them. direct.
Even if you jailbreak the device with full access to the internal files of the system, everything managed by the Secure Enclave chip is protected.

Currently this chip is being equipped on the following Apple devices: from iPhone 5S onwards, from iPad 5th generation to later, from the first generation iPad Air, iPad Mini 2 and later generations, iPad Pro , Mac computers with T1 and T2 chips, Apple TV HD (4th generation) and later, Apple Watch from the first generation, HomePod.
How can vulnerabilities in Secure Enclave cause harm?
In fact, this is not the first time this chip has been attacked to exploit a security hole. In 2017, a group of hackers announced it could decode the Secure Enclave firmware to learn how it works. However, they cannot gain access to the private keys in the chip, so user data remains safe.
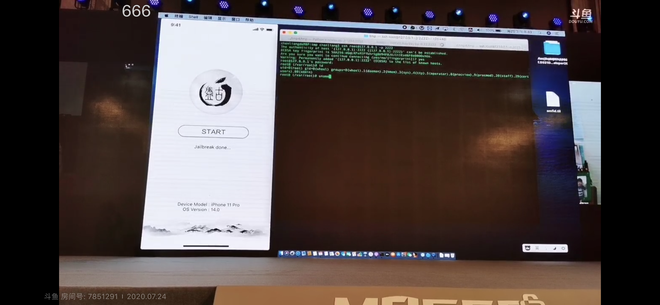
The command line shows that the Pangu Team hacker group from China has access to password and fingerprint data stored in Secure Enclave
Now Chinese hackers from the Pangu Team say they have found a “non-patching” exploit on Secure Enclave that could lead to breaking the encryption layer of the private security keys in the chip. This means there is a flaw in the hardware of this chip, not in the software, and it also means that Apple will not be able to do anything to repair its shipped devices.
While hackers do not know exactly what their exploits are with this flaw, the fact that they have full access to the data on Secure Enclave means that they can also access information about passwords, credit cards and more.
The only thing we know so far is that the flaw in this Secure Enclave affects every generation of Apple chips from A7 to A11 Bionic – similar to the checkm8 vulnerability that allows jailbreaking almost every iOS device from iPhone X go back.
Even if Apple fixed this security hole with chips from A12 and A13 Bionic, there are still hundreds of millions of other Apple devices using chips from A11 Bionic and below that could be at risk by the flaw. exploit this.
However, it is worth noting that these exploits often force hackers to directly access the user’s device to gain data, so it is unlikely that someone uses this method to hack. Remote operation with your device.
Refer to 9to5Mac
Source : Genk
